Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Modern organizations face constant threats ranging from cyberattacks to physical breaches. Conducting a security risk assessment helps businesses identify vulnerabilities, evaluate potential threats, and implement safeguards before incidents occur. A proactive approach not only protects valuable assets but also strengthens operational resilience.
This guide explains the purpose, importance, and best practices for evaluating organizational risks effectively.
A security risk assessment is a structured process that identifies critical assets, analyzes possible threats, and measures the impact of potential incidents. Instead of reacting after damage happens, organizations use this process to anticipate problems and reduce exposure.
It covers digital systems, physical infrastructure, internal processes, and even third-party relationships.
Ignoring risk can lead to data loss, regulatory penalties, and reputational damage. A well-executed evaluation helps organizations:
When businesses regularly examine vulnerabilities, they stay prepared for evolving threats.
To ensure effectiveness, organizations should follow a clear framework:
Begin by listing essential systems, applications, databases, and physical resources. Understanding what needs protection forms the foundation of any protection strategy.
Threats may include malware, phishing attacks, insider misuse, or environmental hazards. Vulnerabilities often involve outdated software, weak passwords, or insufficient employee training.
Determine how likely a threat is to exploit a weakness. Then assess the potential consequences, including operational downtime or financial loss. This step helps prioritize high-risk areas.
Based on findings, implement safeguards such as encryption, firewalls, access controls, monitoring tools, and staff awareness programs. These controls reduce overall exposure.
Risk management is continuous. As technology evolves, organizations must review controls and update policies to address new challenges.
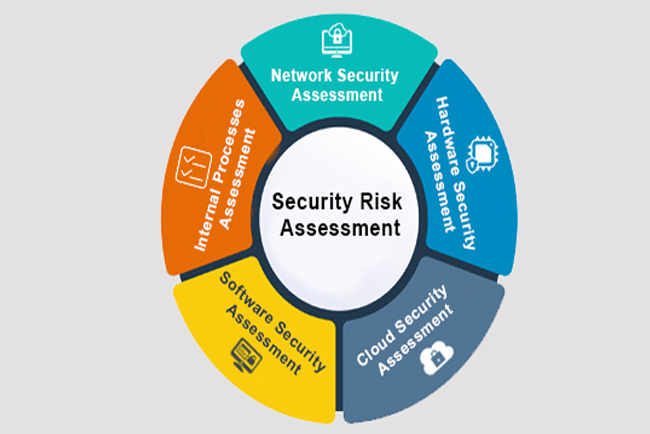
Different industries require different approaches. Common types include:
Selecting the right approach depends on business size, industry standards, and regulatory obligations.
Read More>>Communicable Disease Screening
To maximize effectiveness:
These practices help organizations move from reactive security to proactive defense.
Many organizations struggle with limited budgets, complex digital environments, and rapidly evolving attack methods. Leadership support and employee training play critical roles in overcoming these barriers.
A structured security risk assessment enables organizations to identify vulnerabilities, measure potential impact, and implement targeted controls. By reviewing risks regularly and adapting to new threats, businesses protect their assets and maintain long-term stability.
Proactive risk management is no longer optional. Organizations that invest in systematic evaluations build stronger defenses and gain a competitive advantage in an increasingly digital world.
Read More>>Ronda Rousey vs Gina Carano